If you’re running a WordPress site, keeping it secure is probably one of your top priorities. One often overlooked aspect is how your server communicates its details to visitors and potential hackers. By default, servers often reveal information about their software versions, which can be a security risk. Fortunately, disabling server tokens is a simple but effective step to hide this info and make your site less attractive to malicious actors. In this guide, we’ll walk through what server tokens are, why they matter, and how you can easily disable them to boost your WordPress security.
Understanding Server Tokens and Their Impact on WordPress Security
Let’s start with the basics: what exactly are server tokens? In simple terms, server tokens are pieces of information your web server (like Apache or Nginx) send to visitors about its software version and configuration. Think of it as a badge that says, “Hey, I’m running Apache 2.4.41” or “This server uses Nginx 1.19.” While that information can be useful for debugging or compatibility, it can also be a security vulnerability.
Why is that? Well, revealing your server’s exact software version can help hackers identify specific vulnerabilities associated with that version. For example, if there’s a known security flaw in Apache 2.4.41, an attacker can target that specific version once they know you’re running it. This kind of information disclosure is called “server fingerprinting,” and it gives malicious actors a head start in trying to exploit your site.
Disabling or hiding server tokens essentially means your server won’t broadcast its detailed version info. Instead, it might just say “Server” without specifics, or provide minimal details. This small change can make a significant difference in protecting your WordPress site by reducing the information available to potential attackers.
It’s important to note that hiding server tokens doesn’t secure your server completely—it’s just one layer of security. But combined with other best practices, it can help make your WordPress site less of a tempting target.
3. Reasons to Turn Off Server Tokens in WordPress
When it comes to keeping your WordPress site safe, every little detail counts. One often overlooked security risk is server tokens. But what exactly are server tokens, and why should you consider disabling them? Let’s break it down.
Server tokens are small pieces of information that your web server strings together and sometimes reveal details about the server software and version it’s running. This information can be a goldmine for hackers because it helps them identify potential vulnerabilities specific to that server version.
Here are some key reasons why disabling server tokens makes sense:
- Reduce Information Exposure: By hiding server details, you make it harder for malicious actors to gather intelligence about your setup. The less they know, the less they can exploit.
- Prevent Targeted Attacks: Hackers often scan for servers running outdated or vulnerable versions. Obscuring server information helps protect you from automated scans and targeted exploits.
- Enhance Overall Security Layer: While disabling server tokens isn’t a silver bullet, it’s a simple yet effective step in a comprehensive security strategy.
- Compliance with Security Best Practices: Many security standards recommend hiding server details to minimize attack vectors.
In short, turning off server tokens is about keeping your WordPress environment as secure as possible by not giving attackers any unnecessary clues. It’s a small step that can have a big impact on your overall security posture.
4. Step-by-Step Guide to Disable Server Tokens on Your Server
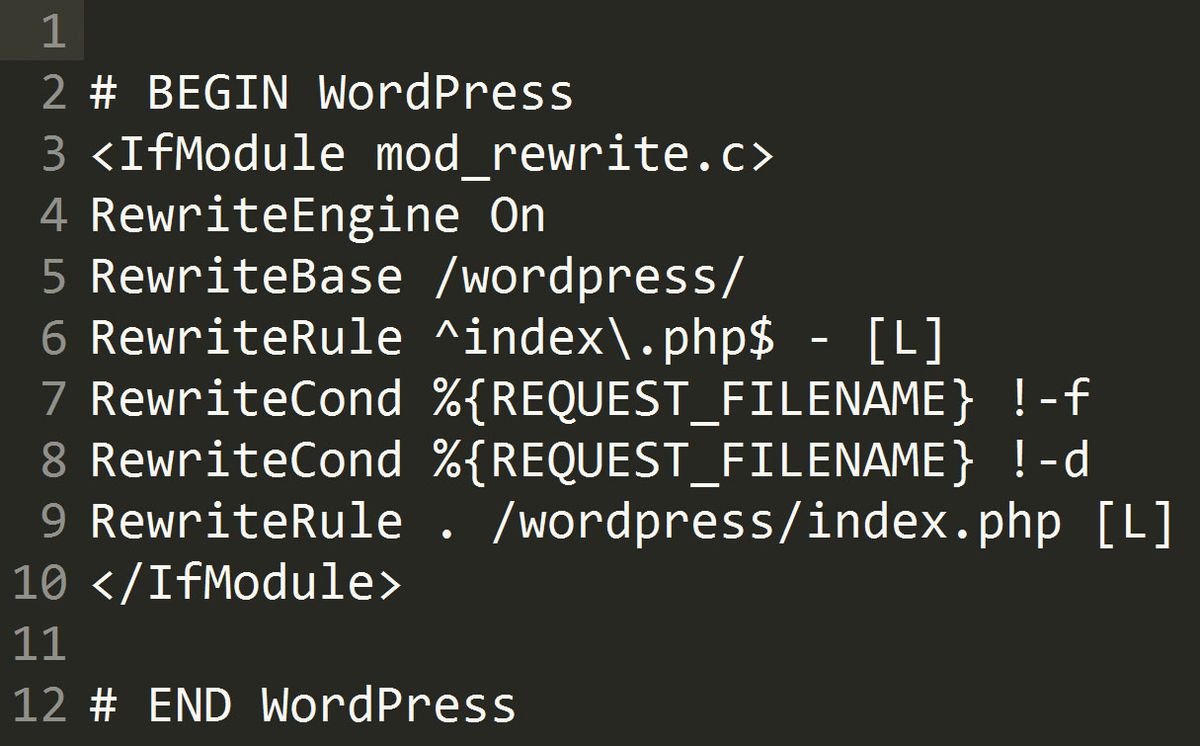
Ready to improve your WordPress security by turning off server tokens? The process varies depending on your server environment, but I’ll walk you through the most common setups: Apache and Nginx. If you’re using a managed hosting provider, you might need to check their documentation or contact support, as some settings may be restricted.
Disabling Server Tokens on Apache
- Access Your Server: Log in via SSH or use your hosting control panel’s terminal feature.
- Locate the Configuration File: Usually, it’s
httpd.confor a file within/etc/httpd/conf/or/etc/apache2/. - Edit the Configuration: Open the file with your preferred editor, e.g.,
nano /etc/apache2/apache2.conf. - Add or Modify the Following Directive:
ServerTokens ProdThis setting tells Apache to only display minimal server information.
- Save and Exit: Save your changes and exit the editor.
- Restart Apache: Apply changes with:
sudo systemctl restart apache2
Disabling Server Tokens on Nginx
- Access Your Server: Log in via SSH.
- Edit the Nginx Configuration File: Typically located at
/etc/nginx/nginx.conf. - Add or Modify the Following Line in the
httpblock:server_tokens off;This directive prevents Nginx from revealing its version in error pages and headers.
- Save the Changes: Save and close the configuration file.
- Test the Configuration: Run
nginx -tto make sure there are no syntax errors. - Reload Nginx: Apply the new setting with:
sudo systemctl reload nginx
Additional Tips
- If you’re using a control panel like cPanel, Plesk, or others, check if they offer a GUI option to disable server tokens.
- Always back up configuration files before making changes.
- After applying the settings, test your server using tools like Security Headers or Hardenize to confirm server details are hidden.
Disabling server tokens is a straightforward yet powerful way to make your WordPress site less visible to potential attackers. Just follow these steps based on your server type, and you’ll be well on your way to a more secure environment!
5. Additional Security Measures for WordPress Websites
While disabling server tokens is a fantastic step toward safeguarding your WordPress site, it’s just one piece of the security puzzle. To really fortify your website, you’ll want to implement a few more best practices that can help prevent common vulnerabilities and keep your site safe from attacks.
First up, keep everything updated. This includes your WordPress core, themes, and plugins. Developers regularly release updates that patch security holes, so staying current minimizes the risk of exploitation. Consider enabling automatic updates if you’re comfortable with that, or set reminders to check for updates regularly.
Next, use strong, unique passwords for all your accounts — especially your admin account. Avoid common passwords like “password123” or “admin.” Incorporate a mix of uppercase, lowercase, numbers, and symbols. Using a password manager can help generate and store complex passwords securely.
Another crucial step is to limit login attempts. Brute-force attacks often target login pages, trying numerous password combinations. Plugins like Wordfence or Login Lockdown can help restrict login attempts and block suspicious IP addresses after too many failed tries.
Implementing SSL certificates is also essential. HTTPS encrypts data transmitted between your visitors and your server, protecting sensitive information like login credentials. Most hosting providers offer free SSL certificates via Let’s Encrypt, and setting this up is straightforward.
Consider adding a firewall to your WordPress setup. Web Application Firewalls (WAFs) monitor and filter incoming traffic, blocking malicious requests before they reach your site. Many security plugins include firewall features, or you can opt for a dedicated WAF service.
Finally, regular backups are your safety net. In case of a security breach or data loss, having recent backups means you can restore your site quickly without losing everything. Use reputable backup plugins or hosting solutions that offer automated backups to keep your data safe.
By layering these additional security measures with your disabled server tokens, you’ll significantly reduce your website’s vulnerability. Remember, security isn’t a one-time setup but an ongoing process. Stay vigilant, keep learning, and regularly review your security practices to ensure your WordPress site remains a safe haven for your visitors.
6. Conclusion and Best Practices for Securing Your WordPress Site
Securing your WordPress website might seem overwhelming at first, but taking methodical steps like disabling server tokens can make a real difference. Remember, the goal is to make your site a less attractive target for hackers and bots by minimizing the information they can glean and reinforcing your defenses.
Here’s a quick rundown of best practices to keep your WordPress site secure:
- Disable server tokens to prevent revealing server details.
- Keep everything updated — core, themes, plugins.
- Use strong, unique passwords and enable two-factor authentication when possible.
- Limit login attempts to thwart brute-force attacks.
- Implement SSL certificates for encrypted data transmission.
- Install security plugins that offer firewalls, malware scanning, and login monitoring.
- Regularly back up your website so you can restore quickly if needed.
- Remove unused themes and plugins to reduce attack surfaces.
- Set correct file permissions to prevent unauthorized access.
Security is an ongoing journey, not a one-time setup. Regularly review your security measures, stay informed about new vulnerabilities, and respond promptly to any alerts or suspicious activity. By doing so, you’ll create a safer environment for your visitors and protect your hard work from cyber threats.
Remember, a secure website not only protects your data but also builds trust with your audience. So, invest the time today to implement these best practices, and enjoy peace of mind knowing your WordPress site is as secure as possible.