When managing your WordPress site, security should always be a top priority. One aspect that often gets overlooked is the server tokens — little pieces of information your server reveals about itself. These tokens can tell potential attackers what software and version you’re running, which might make it easier for them to find vulnerabilities. By understanding and controlling server tokens, especially by turning them off, you can reduce the risk of exposing sensitive details. Think of it like hiding your home’s address — less info, less risk. Let’s explore what server tokens are and why turning them off can make your site safer.
Understanding the HTTP Header Plugin in WordPress
The HTTP Header Plugin is a handy tool for WordPress users who want to customize the HTTP headers sent by their server. Headers are like info cards that tell browsers and other servers how to handle your website. With this plugin, you can easily add, modify, or remove headers without diving into complex server configurations. It’s especially useful for adding security headers, such as disabling server tokens, which can help hide your server details from prying eyes. The plugin’s user-friendly interface makes it simple for both beginners and experienced site owners to tweak header settings, giving you more control over your site’s security and performance. In this guide, we’ll walk through how to use the plugin to turn off server tokens and boost your WordPress site’s security posture.
3. Steps to Disable Server Tokens in Your Server Configuration
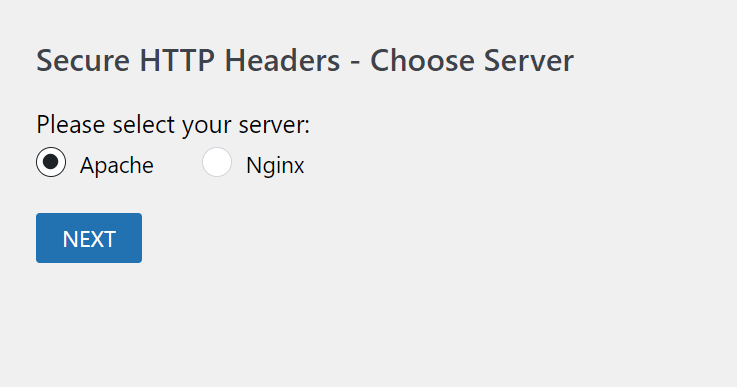
Disabling server tokens is a smart move if you want to enhance your website’s security by hiding server version details from potential attackers. The process varies depending on your server environment, but let’s walk through the typical steps for popular servers like Apache and Nginx.
For Apache Servers
Apache servers often display server version info in headers, which can be exploited. To turn off server tokens:
- Access your server’s configuration file: Usually located at
/etc/apache2/apache2.confor/etc/httpd/conf/httpd.conf. - Find the line that starts with
ServerTokens. If it doesn’t exist, add it. - Set the value to
Prod, which suppresses detailed version info:
ServerTokens ProdBy setting it to Prod, Apache will only display minimal info like “Apache” instead of version numbers.
- Disable ServerSignature: To prevent server signatures on error pages, add or modify this line:
ServerSignature OffSave the file and restart Apache:
sudo systemctl restart apache2 Debian/Ubuntusudo systemctl restart httpd CentOS/RedHatThis will hide detailed server info from headers and error pages.
For Nginx Servers
In Nginx, you can remove or modify the header that reveals server info:
- Edit your Nginx configuration file, typically located at
/etc/nginx/nginx.conf. - Add or modify the line inside the
http {}block:
server_tokens off;This directive disables the detailed server version in error pages and headers.
- Save your changes and restart Nginx:
sudo systemctl restart nginxNow, your server won’t reveal detailed version info, making it less attractive to potential attackers.
4. Configuring Server Tokens Off Using the HTTP Header Plugin
If you’re using WordPress and prefer a more straightforward way to manage headers without diving into server configs, the HTTP Header plugin is a fantastic option. It allows you to easily add, modify, or remove headers, including those that reveal server info.
Getting Started with the HTTP Header Plugin
First, install and activate the plugin:
- Go to your WordPress admin dashboard.
- Navigate to Plugins > Add New.
- Search for HTTP Headers or a similar plugin.
- Install and activate it.
Disabling Server Tokens via the Plugin
Once the plugin is active, you can configure headers to hide server details:
- Navigate to the plugin’s settings page, usually under Settings > HTTP Headers.
- Look for an option to add custom headers or modify existing ones.
- Add a new header:
Name: ServerValue: HiddenThis effectively overrides the default server header, making it less informative.
Using the Plugin to Remove or Mask Server Headers
Some header plugins allow you to completely remove certain headers:
- If available, select the option to remove the
Serverheader. - If removal isn’t available, set the
Serverheader to a generic value like Apache or Nginx.
Be sure to save your changes after configuring the headers.
Additional Tips
- Always back up your site before making significant changes.
- Test your website after configuration to ensure headers are correctly set.
- Use online header checkers like WebConfs to verify your headers.
By managing headers through the HTTP Header plugin, you can effectively hide your server version and make your WordPress site more secure without touching server files directly. It’s a simple, user-friendly way to keep your site safer from unwanted scrutiny.
5. Verifying That Server Tokens Are Successfully Disabled
Once you’ve made the changes to disable server tokens in your server configuration via the HTTP Header plugin, it’s essential to verify that everything is set up correctly. After all, you want to make sure that your server isn’t revealing unnecessary information that could be exploited by hackers.
The easiest way to check this is by using online tools or command-line utilities. Here are some simple methods you can try:
Using Online Header Checkers
- Navigate to websites like WebConfs HTTP Header Check or Security Headers.
- Enter your website URL and run the scan.
- Review the output for the Server header. If your server tokens are correctly disabled, you should see something like Server: Apache or nginx without version details or additional info.
Using Command-Line Tools
If you’re comfortable with terminal commands, you can use curl to inspect the headers directly:
curl -I https://yourwebsite.comThis command fetches the HTTP headers for your site. Look for the Server header. It should look like:
Server: Apacheor
Server: nginxwithout any version numbers or detailed info. If you see version numbers like Apache/2.4.41 (Ubuntu) or similar, it means the server tokens are still enabled.
Interpreting the Results
If your verification shows that server details are hidden or minimized, congratulations! You’ve successfully disabled server tokens. If not, double-check your server configuration and the plugin settings. Sometimes, server restarts are necessary for changes to take effect.
Remember, hiding server details is a simple yet effective step toward improving your website’s security posture. Regularly verifying your headers helps ensure your server remains as secure as possible.
6. Additional Security Tips for WordPress Websites
Disabling server tokens is just one piece of the security puzzle. To keep your WordPress site safe from threats, consider implementing these additional best practices:
1. Keep Everything Up to Date
- Always update WordPress core, themes, and plugins to the latest versions. Developers regularly patch security vulnerabilities, so staying current is crucial.
2. Use Strong, Unique Passwords
- Ensure all user accounts, especially admin accounts, have strong passwords. Consider using a password manager to generate and store complex passwords.
3. Limit Login Attempts
- Install plugins like Limit Login Attempts Reloaded to prevent brute-force attacks by locking out IPs after several failed login tries.
4. Enable Two-Factor Authentication (2FA)
- Adding 2FA adds an extra layer of security. Plugins like Google Authenticator or WP 2FA make it easy to set up.
5. Use HTTPS Everywhere
- Secure your site with an SSL certificate. Many hosting providers offer free SSL (like Let’s Encrypt). Enforce HTTPS to encrypt data transmitted between your server and visitors.
6. Regular Backups
- Schedule regular backups of your site and database. Tools like UpdraftPlus or BackupBuddy make restoring your site quick and easy if needed.
7. Harden Your wp-config.php and .htaccess Files
- Move wp-config.php to a non-web-accessible directory if possible.
- Restrict access to important files via .htaccess rules, such as denying access to wp-includes and wp-admin directories.
8. Disable File Editing in WordPress Dashboard
- Add this line to your wp-config.php:
define('DISALLOW_FILE_EDIT', true);to prevent users from editing files through the admin panel.
9. Install Security Plugins
- Consider tools like Wordfence Security or Sucuri Security for real-time scanning, firewall protection, and malware removal.
10. Monitor Your Site
- Regularly check your site’s security logs and use tools like Google Search Console to identify potential issues.
By combining these practices with server token hiding, you’ll significantly enhance your WordPress website’s defenses against common vulnerabilities and attacks. Remember, security is an ongoing process, so stay vigilant and proactive in protecting your online presence.
Conclusion and Best Practices for Enhancing Website Security
Disabling server tokens is a crucial step in minimizing the information exposed to potential attackers. By turning off server tokens in WordPress using the HTTP Header plugin, you effectively obscure server details, reducing the risk of targeted exploits. However, this should be part of a comprehensive security strategy. Always keep your WordPress core, themes, and plugins up to date, and implement strong, unique passwords for all user accounts. Regularly review your security settings and logs to detect any suspicious activity early.
Here are some best practices to further enhance your website’s security:
- Use HTTPS: Ensure your site is served over SSL/TLS to encrypt data transmission.
- Implement a Web Application Firewall (WAF): Protect your site from malicious traffic and attacks.
- Limit Login Attempts: Prevent brute-force attacks by restricting login retries.
- Disable Directory Listing: Prevent attackers from viewing directory contents.
- Regular Backups: Maintain recent backups to restore your site quickly in case of a breach.
By combining server token concealment with these security measures, you significantly strengthen your WordPress site’s defenses against common threats. Remember, security is an ongoing process that requires vigilance and regular updates to stay ahead of emerging vulnerabilities.